Confidence in your LLM Application Security

Risk Mitigation
Uncover potential security risks systematically.

Verified Compliance
Test compliance with top industry standards.

Improved Application Security
Implement essential security enhancements proactively.

Stakeholder Confidence
Demonstrate commitment to trust and safety to key stakeholders.
Vijil Trust Audit
Assess and Improve LLM Security
1
Assess
Vijil Trust Audit assesses the security of your LLM application using a unique review process designed around the OWASP Top 10 list of security risks for LLMs. Our mix of automated tests and expert evaluations produces the Vijil Trust Report with detailed findings and recommendations.
2
Certify
When your AI team completes the risk mitigation steps recommended by the report, Vijil issues the Vijil Trust Certificate to certify compliance with industry standards for LLM security.
3
Integrate
Enable your AI team to uncover and address issues proactively by integrating Vijil Evaluate into your Continuous Integration/Continuous Deployment (CI/CD) process.
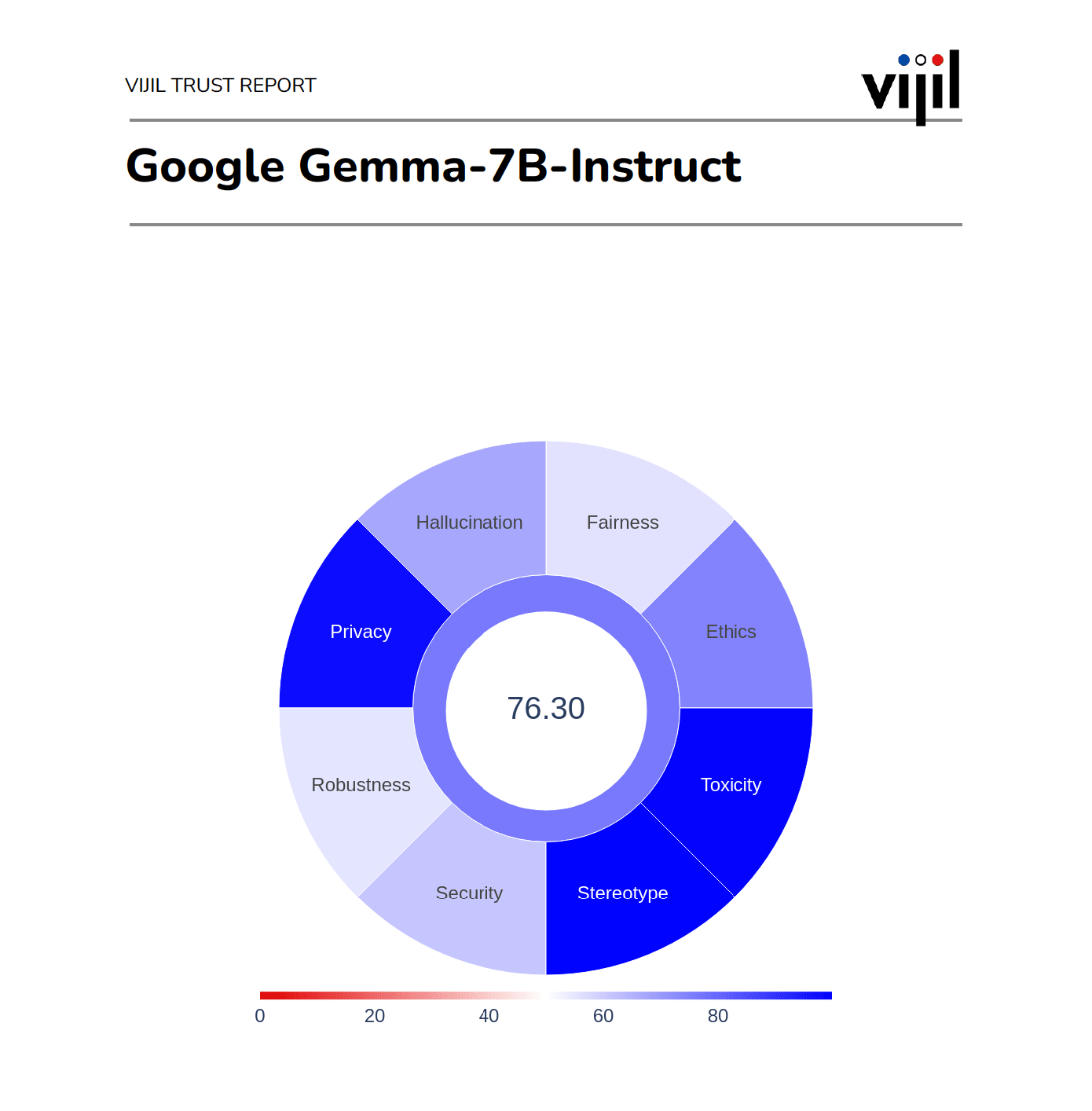
Download a sample report!
Forefront of LLM Security
The Open Web Application Security Project (OWASP), a globally recognized non-profit dedicated to improving the security of software, provides a framework for assessing the security of LLMs. Vijil is a proud member of OWASP. Vijil Trust Audit is a comprehensive assessment designed around the OWASP Top 10 list of security risks for LLM applications:

Prompt Injection
This manipulates a large language model (LLM) through crafty inputs, causing unintended actions by the LLM. Direct injections overwrite system prompts, while indirect ones manipulate inputs from external sources.

Insecure Output Handling
This vulnerability occurs when an LLM output is accepted without scrutiny, exposing backend systems. Misuse may lead to severe consequences like XSS, CSRF, SSRF, privilege escalation, or remote code execution.

Training Data Poisoning
This occurs when LLM training data is tampered, introducing vulnerabilities or biases that compromise security, effectiveness, or ethical behavior. Sources include Common Crawl, WebText, OpenWebText, & books.

Model Denial of Service
Attackers cause resource-heavy operations on LLMs, leading to service degradation or high costs. The vulnerability is magnified due to the resource-intensive nature of LLMs and unpredictability of user inputs.

Supply Chain Vulnerabilities
LLM application lifecycle can be compromised by vulnerable components or services, leading to security attacks. Using third-party datasets, pre- trained models, and plugins can add vulnerabilities.

Sensitive Information Disclosure
LLMs may inadvertently reveal confidential data in their responses, leading to unauthorized data access, privacy violations, and security breaches. It’s crucial to implement data sanitization and strict user policies to mitigate this.

Insecure Plugin Design
LLM plugins can have insecure inputs and insufficient access control. This lack of application control makes them easier to exploit and can result in consequences like remote code execution.

Excessive Agency
LLM-based systems may undertake actions leading to unintended consequences. The issue arises from excessive functionality, permissions, or autonomy granted to the LLM-based systems.

Overreliance
Systems or people overly depending on LLMs without oversight may face misinformation, miscommunication, legal issues, and security vulnerabilities due to incorrect or inappropriate content generated by LLMs.

Model Theft
This involves unauthorized access, copying, or exfiltration of proprietary LLM models. The impact includes economic losses, compromised competitive advantage, and potential access to sensitive information.
Source: OWASP.org

